Customer Journey Security
Protection from evolving fraud, bots, and AI
Spec prevents missing, blocked, and manipulated data from exposing your business to dynamic attacks.
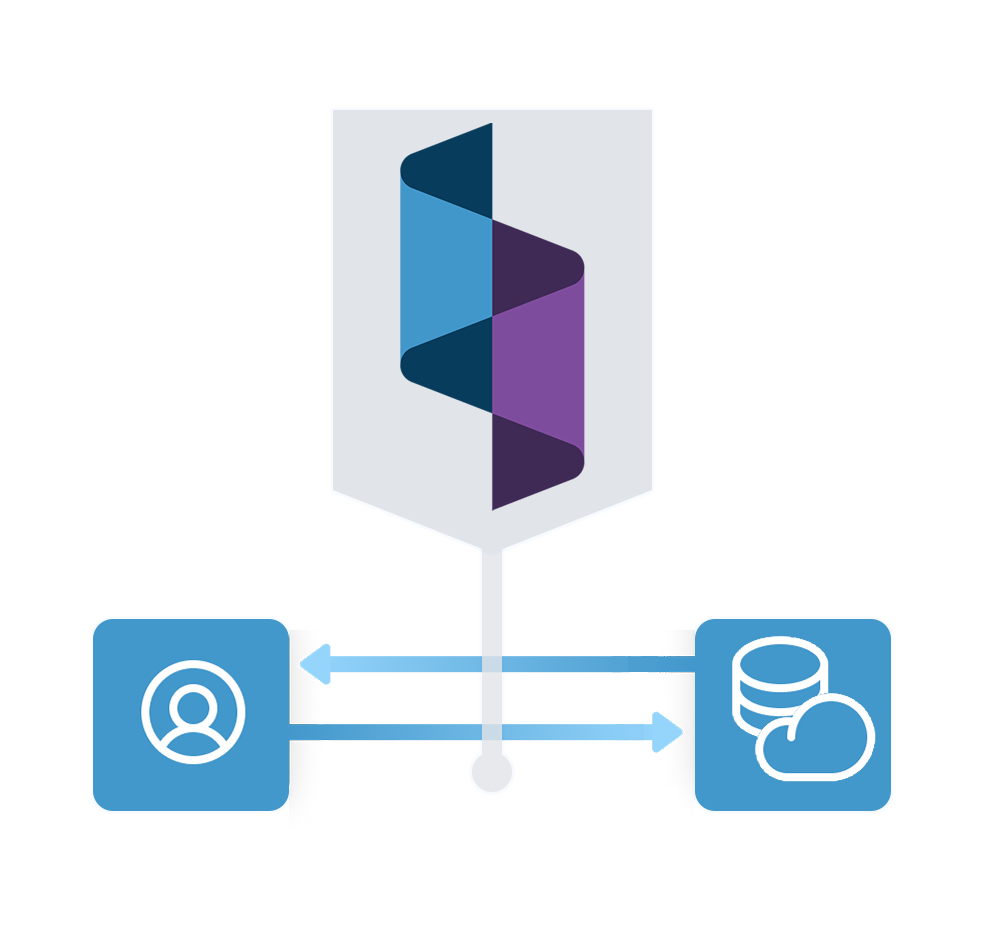
Platform Features
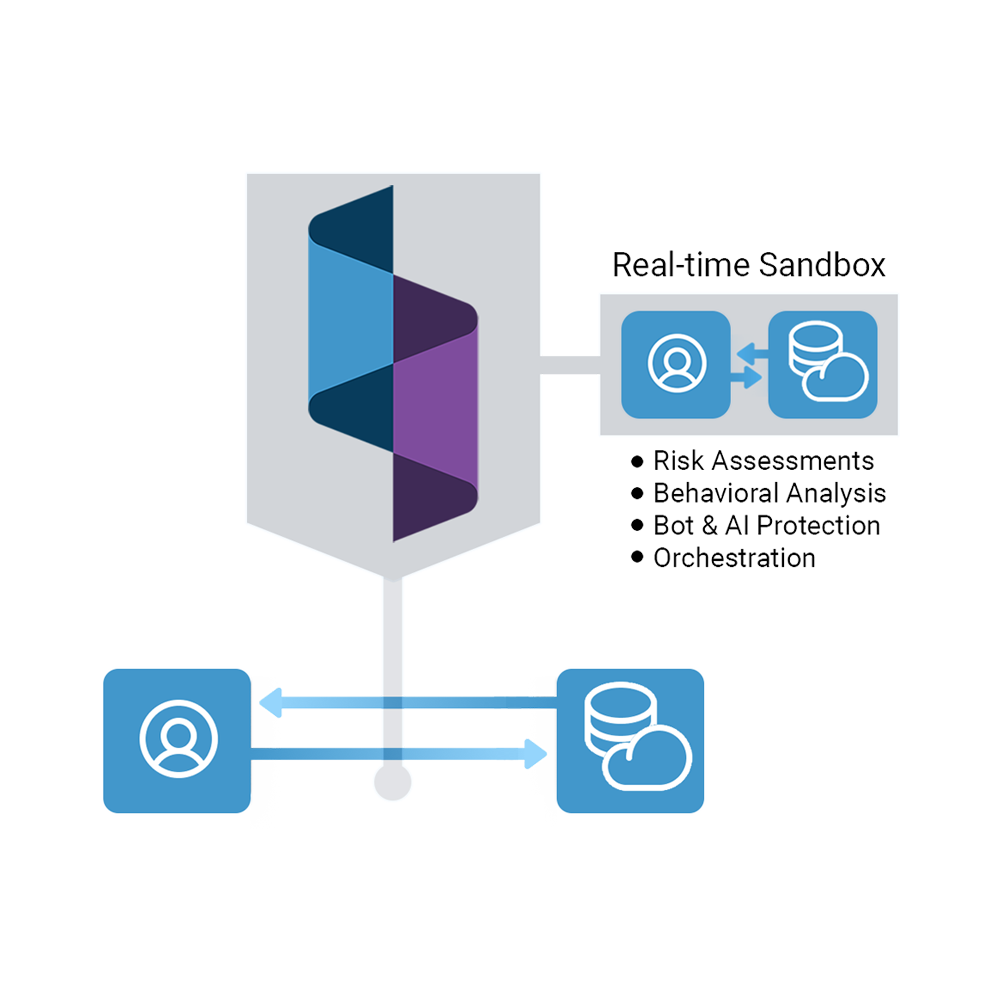
Protects with 14x the data
Spec collects and links complete journey data that’s beyond the reach of legacy defenses.
Invisible and tamper-proof
Spec monitors user activity and attacker tampering attempts without touching the user experience.
Honeypots attackers
Spec uses honeypots to blind attackers, harvest their tactics, and prevent them from learning.
Consumer privacy tools and AI-powered bots make it impossible to trust the data you used to rely on.
On the Spec Platform

Limitless integrations
Spec effortlessly updates your existing tools and workflows with customer journey data in real time.
See the platform in action
Get started with a demo of the Spec platform, then get an end-to-end report of your customer journeys and the sources of attack pressure against them.